An attacker logs into my RDP Honeypot, launches Advanced Port Scanner, attempts to run a Meterpreter reverse shell; and then, dumps Lsass using ProcDump. The attacker, stumbles along the way and does not accomplish their mission. See the timeline, details, summary and IOCs below.
Timeline
2:52 – Logon from 185.156.177[.]131
2:55 – Copied Advanced Port Scanner to the system and then ran it.
3:42 – Defender blocks wusx.exe and associates it to Meterpreter

VT score for wusx.exe

If the attacker would have been able to run wusx.exe, it would have made two attempts to talk back to 193.188.22[.]110 over TLS, which I assume, would have given the attacker a Meterpreter shell.
Here’s a sandbox run of wusx.exe Any.Run
4:20 – procdump64.exe is copied and ran on the system to dump Lsass.

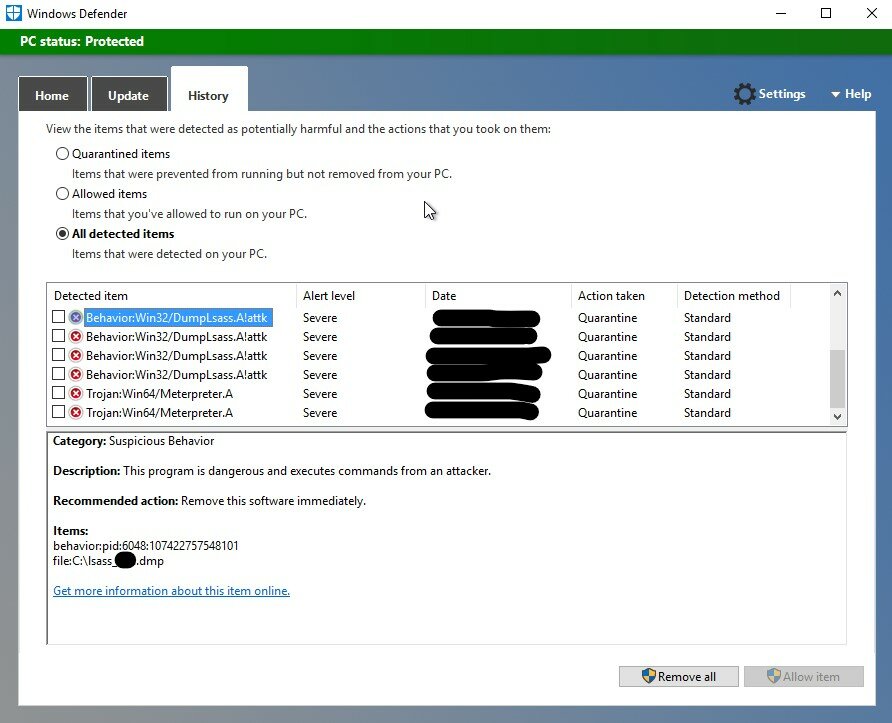
4:20 – Defender quarantines the lsass dmp file. This is the first time I’ve seen this and I was a little confused when it happened. A different attacker did the same thing a couple weeks ago and was able to exfil the dmp file but not this time. Good thing the attacker didn’t know they could just unquarantine it 😉 . The attacker tried this command multiple times and each time Defender quarantined the file.

Defender quarantining the lsass dmp file.

4:24 – winrar-x64-580ru.exe was copied and installed. This seems to be the regular installer but in Russian language. I assume they were going to zip the dmp before exfiling, but they never got a chance to grab the dmp file.
4:25 – Tries to dump Lsass a final time but it fails.
4:26 – Attacker logs out
Summary
Use Defender. I’m quite impressed that the built-in Defender AV is able to do this. This same attack happened a couple weeks ago and Defender let it go. I would recommend you use Defender AV in Windows 10 over any of the free choices or out-of-date, third-party versions. This attacker did not seem very intelligent because they could have very easily turned-off Defender or quarantined the files, as they were running as admin. If you are using Defender AV, not with ATP, make sure you centralize logs so you have visibility into these types of detections.
Here is a Sigma rule to detect lsass being dumped: win_susp_procdump.yml This would have fired when procdump dumped lsass based on the command line syntax. If you would like to check out more about procdump/lsass check out the CAR report by MITRE here.
IOCs
Source IP – 185.156.177[.]131
WinRAR (RU version) – Same version and hash from rarlab.com