An attacker logged into the honeypot, dropped XMRig and mimikatz, and then ran XMRig. XMRig installed Netshta to maintain persistence and then started mining Monero. When the attacker dropped mimikatz, they accidentally dropped a list of usernames, passwords and IPs. See below for info on XMRig, intrusion summary, OPSEC fail, and IOCs.
XMRig
XMRig is a
High performance, open source, cross platform RandomX, CryptoNight and Argon2 CPU/GPU miner, with official support for Windows.
XMRig is used to mine Monero. It didn’t run very long on our honeypot but we decided to trace the user/wallet and found that they have mined 7.62785295 XMR, over the last 400 days. That equates to $486. Here is the payment history for this user/wallet.

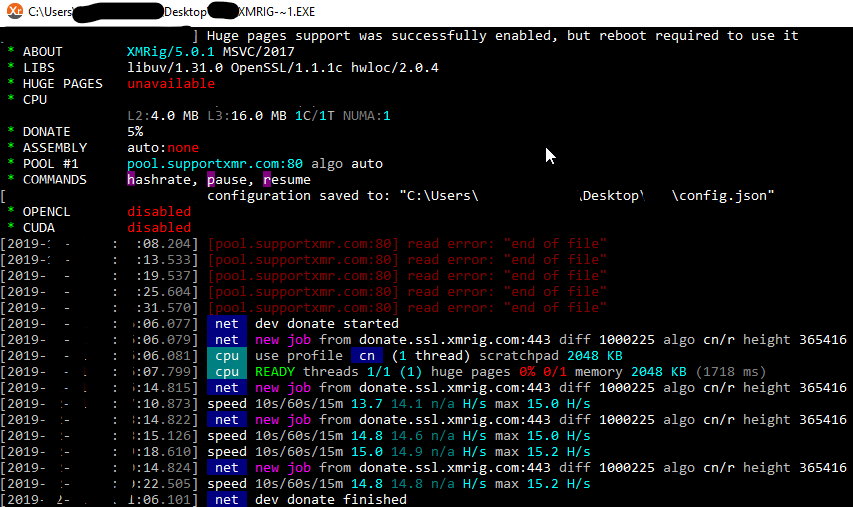
Here’s XMRig running

Here’s part of the XMRig configuration file, which includes the user, password and pool.

Intrusion Summary
Attacker logged in from 178.131.149.179
They drop mimikatz and xmrig


When xmrig.exe ran, it dropped a couple files and created a registry key for persistence. Xmrig created svchost.com, which then created directx.sys, which can be seen below.

svchost.com is known as Neshta. Netshta uses process injection to inject itself into a process found in the directx.sys file. Here are the contents of directx.sys

This is the registry key set by xmrig to maintain persistence through svchost.com. Every time an exe is opened or launched svchost.com will run.

This is what it looks like after the above command is run

Even though mimikatz was never run, the attacker did come back later, looking to continue their operation; however, we had already reset the environment. Defender was off during these events, but if it were on, it would have blocked XMRig and mimikatz.
XMRig Review
We loaded XMRig into PEStudio and could see: that it was well known on VT, in a Russian language, and referenced many blacklisted strings.

Here are some of the strings that were blacklisted.

Neshta Review
Next, we loaded svchost.com (Neshta) into PEStudio

You can see here that svchost.com accesses the ShellExecuteA API to execute shellcode directly into a process.

This is a string we found at the very bottom of the exe.

OPSEC Fail
When the attacker copied over mimikatz, they also copied over a couple txt files with a bunch of usernames, passwords, and IPs. Are you familiar with what tool output these files? If so, contact us.


You’ll notice that most of the passwords are easy to guess/brute force so I assume this person or group either bought this information to install XMRig or they go around brute forcing RDP, installing XMRig and collecting credentials. We didn’t see any attempts to check domain status or dump creds.
Here is a picture of the IPs geo-location. You’ll notice there is a heavy concentration in China (~66 IPs).

All for now!
IOCs
Attacker IP – 178.131.149.179
svchost.com – VT
mimikatz.exe – VT
xmrig.exe – VT
Reg key persistence – reg key create “exefile\shell\open\command” + “%1” + “%*”