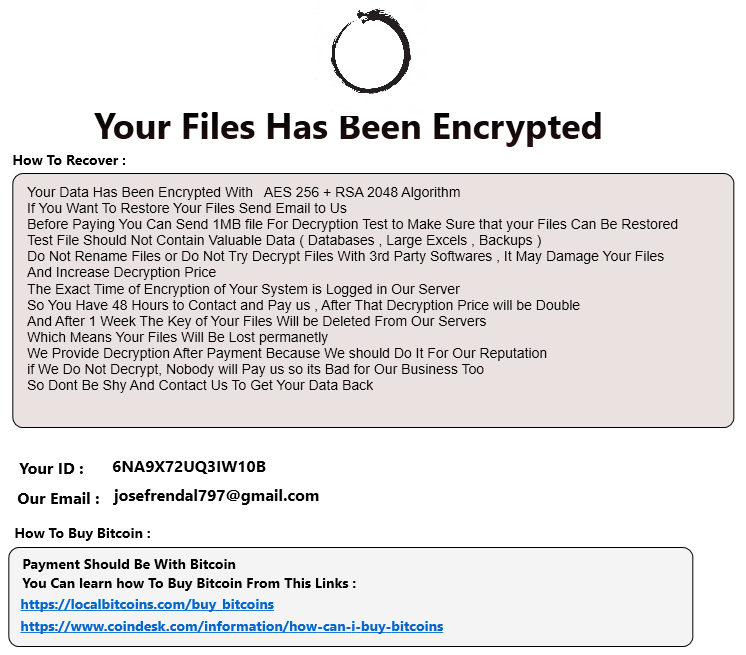
The attacker logged in from 64.44.81[.]20 and dropped two files. One named ours.zip and the other named 2284JS_payload.zip. They then attempted to extract these files numerous times but Defender blocked them. The attackers were not successful in their mission of deploying ransomware on the system.
Here’s some brief information on the two variants and IOCs.
Harma
Harma (2284JS_payload.zip) is a variant of Dharma/CrySiS. There is not a decryptor for this variant. More info can be found at BleepingComputer and BleepingComputer#2


Here’s an interesting pdb path.

Odveta
Odveta (ours.zip) is a variant of Ouroboros. There is not a decryptor for this this variant. More info can be found at BleepingComputer and Bitdefender.


Another interesting pdb path.

This variant runs a slew of commands before initiating the ransomware such as killing mssql and mysql.

Wonder how common it is for curse words to be included in binaries…

Summary
This was a smash and grab attempt with the attacker only being logged in for ~5 minutes. The attackers IP is located in the US so make sure you aren’t only looking at foreign traffic. Although the attacker was not successful they did change the password which I assume means they will be back. I thought it was interesting that they dropped two ransomware variants and even more interesting that one was called “ours”. Wonder if this has anything to do with RaaS (Ransomware as as Service) 😉
IOCs
All IOCs in MISP Priv Event ID 65218 or UUID 5e66dd0a-d858-4f9e-b0b2-a7c6950d210f via CIRCL OSINT feed.
Any.Run – ours.exe , 2284JS_payload.exe
VT – ours.exe, 2284JS_payload.exe