**If you’ve been contacted by me, it is because your device is on the internet and may be vulnerable to the vulnerabilities identified below. Please read through this and contact me if you have questions. Thanks** What is Tridium Niagara? Tridium is the developer of Niagara Framework. The Niagara Framework is a universal software infrastructure…
Author: JW
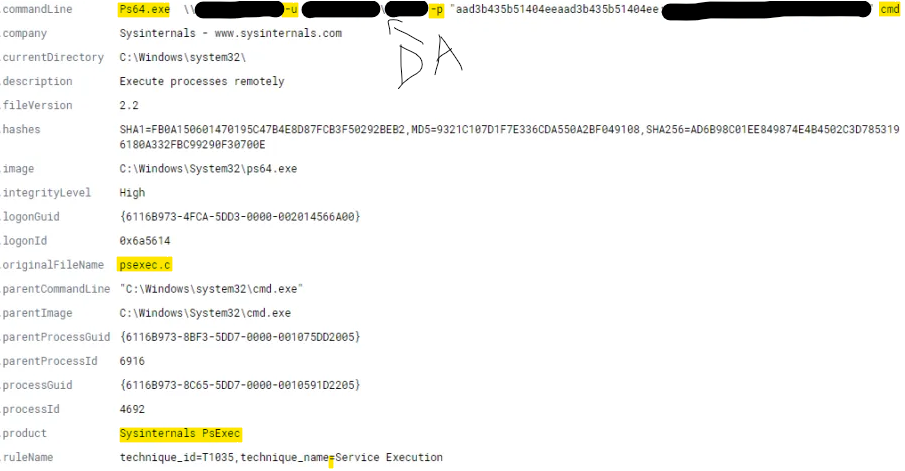
From Zero to Lateral Movement in 36 Minutes
An attacker logged into the RDP Honeypot a few weeks ago and was able to dump credentials and move laterally in 36 minutes. I’ve been seeing more and more ProcDump and less and less mimikatz lately. The attacker attempted to run a couple executables to maintain persistence but these attempts failed. These attempts failed because…
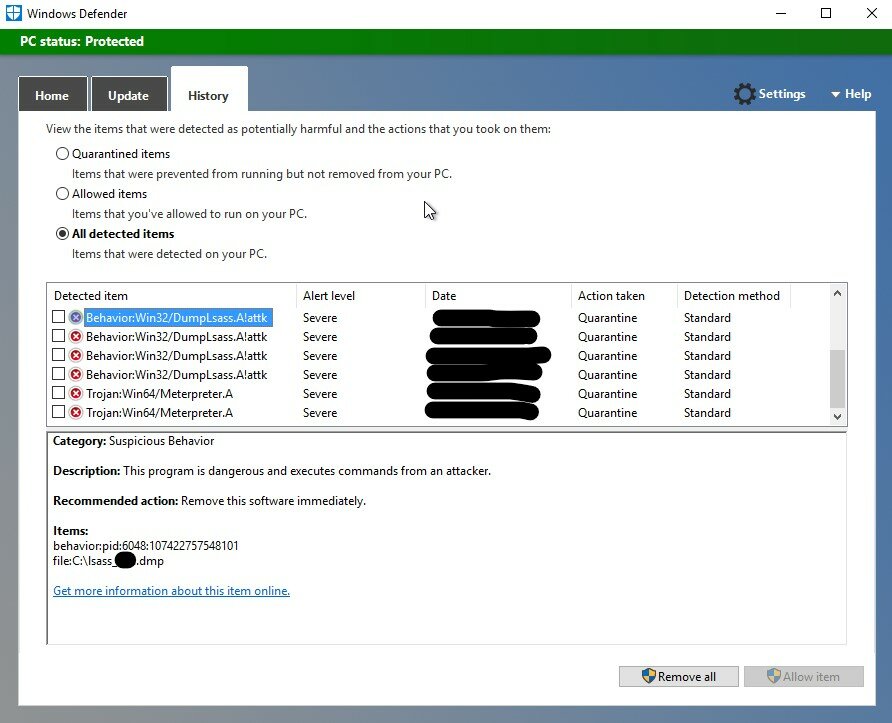
Defender Quarantines Lsass Dumps
An attacker logs into my RDP Honeypot, launches Advanced Port Scanner, attempts to run a Meterpreter reverse shell; and then, dumps Lsass using ProcDump. The attacker, stumbles along the way and does not accomplish their mission. See the timeline, details, summary and IOCs below. Timeline 2:52 – Logon from 185.156.177[.]131 2:55 – Copied Advanced Port…
Debit vs Credit Cards
During the holidays, I occasionally get asked by family and friends if it’s safer to use debit or credit cards. In my opinion, this is an easy answer but instead of repeating the conversation numerous times, I decided to write a short blog about it. So the first question is, what is the difference between…
Defending Against Emotet
Emotet started making the rounds again a couple months ago. If you work in an enterprise environment you’ve probably seen a sample or two. Here’s an in depth write-up by Brian on Emotet TTPs. Here are a few things you can do to defend against Emotet: Block Macros Block macros from running in Word files…
RDP Honeypotting
I recently stood up a RDP honeypot consisting of a Windows VM with Wazuh and Sysmon. SecurityOnion is setup to monitor traffic to/from the internet for the honeypot. A UTM device is sitting between the honeypot and the internet to block ports, applications and proxy all traffic. I haven’t setup ssl decryption yet but I’m…
MouseJack: From Mouse to Shell – Part 2
This is a continuation of Part 1 which can be found here. New/Fixed Mice Since the last blog post, I’ve done some additional testing and it looks like most of the newer wireless mice are not vulnerable to MouseJack. I tested the best-selling wireless mouse on Amazon (VicTsing MM057), Amazon’s choice (AmazonBasics), and one of…
MouseJack: From Mouse to Shell – Part 1

What is MouseJack? MouseJack is a class of vulnerabilities that affects the vast majority of wireless, non-Bluetooth keyboards and mice. These peripherals are ‘connected’ to a host computer using a radio transceiver, commonly a small USB dongle. Since the connection is wireless, and mouse movements and keystrokes are sent over the air, it is possible…
Securing Your Online Accounts with 2FA

As the holidays came and went I was asked one question by family and friends more than any other. How do I keep my accounts secure? If you work in InfoSec you know this isn’t an easy question to answer but there are a few things everyone can do to secure their online accounts. Nothing…
Here are instructions for enabling two factor authentication (2FA) on Twitter: Login to Twitter Click Profile and Settings next to Tweet on the top right, then click settings and privacy Click Set up login verification under the Security heading Add your phone number and click send code Click get backup code and save this in…