This script was dropped and run in the honeypot recently. Here are a couple takeaways and a screenshot of the script. @iranofficall / User Creator Adds 4 users Sets passwords to $95But6nL03 Sets passwords to never expire Enables RDP Hides accounts from sign-in screen Possible Detections Command arguments contains /maxpwage:unlimited Process net.exe + command arguments…
Category: RDP Honeypot
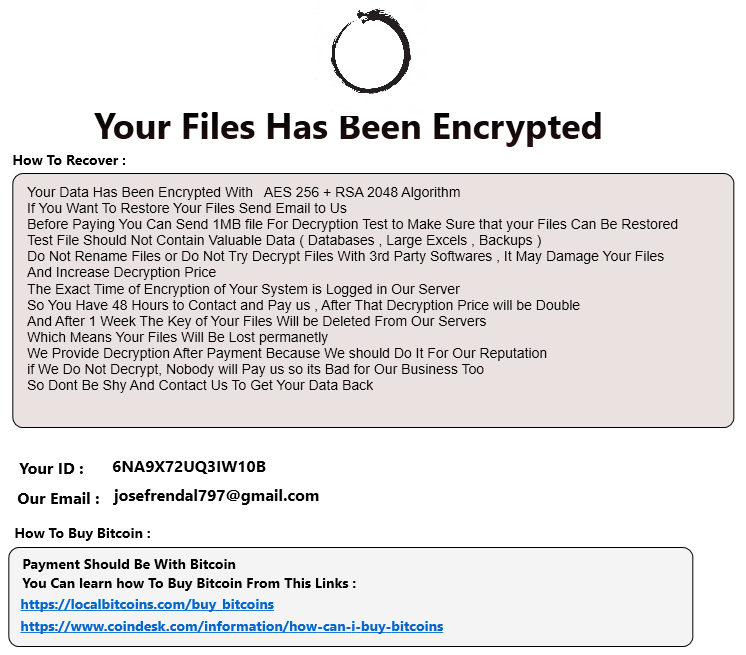
Harma and Odveta Ransomware
The attacker logged in from 64.44.81[.]20 and dropped two files. One named ours.zip and the other named 2284JS_payload.zip. They then attempted to extract these files numerous times but Defender blocked them. The attackers were not successful in their mission of deploying ransomware on the system. Here’s some brief information on the two variants and IOCs….
Trickbot and AdFind Recon
An attacker logged into the honeypot, dropped AdFind, a couple batch files and Trickbot. The attacker created a user, ran a recon script utilizing AdFind and then installed Trickbot. This is what the folder structure looked like. Timeline Time in UTC 22:13 – login from 216.170.123[.]19 22:15 – opens powershell and runs the following command…
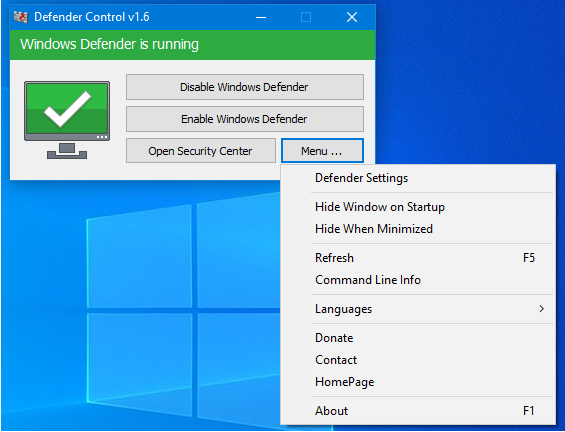
VBS Downloader and Defender Control
An attacker logged into the honeypot and ran a batch file that created a vbs script that attempted to download a possible coin miner. The download was blocked by the content filtering system but the attacker seemed to think Defender blocked it. The attacker then downloaded an application named Defender Control to turn off Defender….
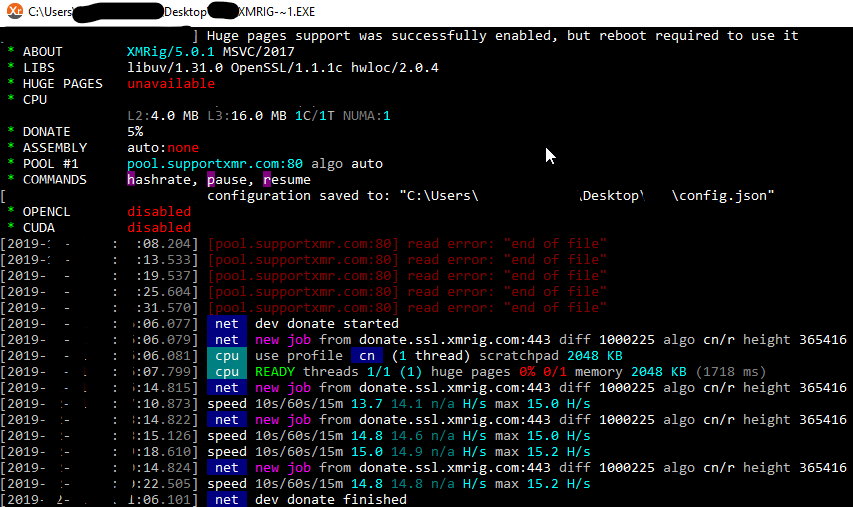
XMRig and OPSEC Fail
An attacker logged into the honeypot, dropped XMRig and mimikatz, and then ran XMRig. XMRig installed Netshta to maintain persistence and then started mining Monero. When the attacker dropped mimikatz, they accidentally dropped a list of usernames, passwords and IPs. See below for info on XMRig, intrusion summary, OPSEC fail, and IOCs. XMRig XMRig is…
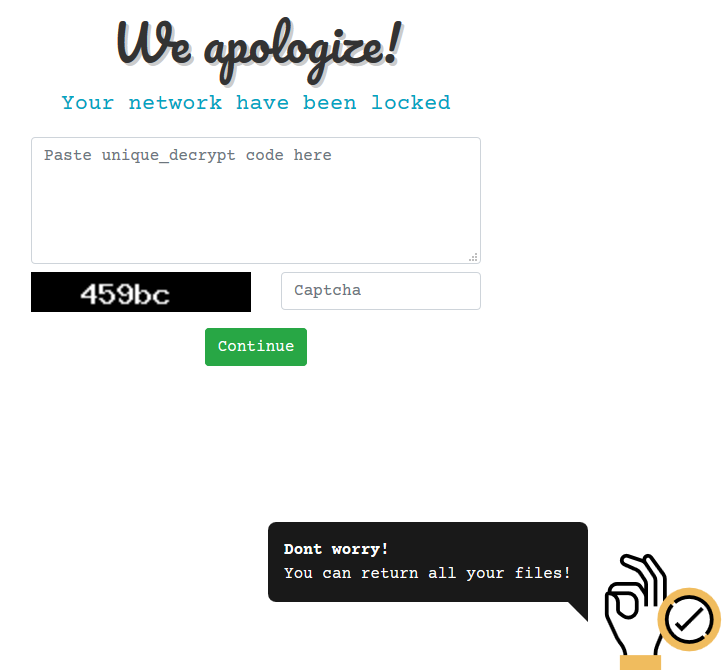
Ako Ransomware
An attacker logged into the RDP Honeypot and quickly ran Ako Ransomware. The attacker had opened the Defender GUI to disable it–but a bot from the previous day had already disabled it. The attacker then dropped Locker.exe, ran it, and then logged off before the execution had completed. Locker.exe is also known as Ako and…
From Zero to Lateral Movement in 36 Minutes
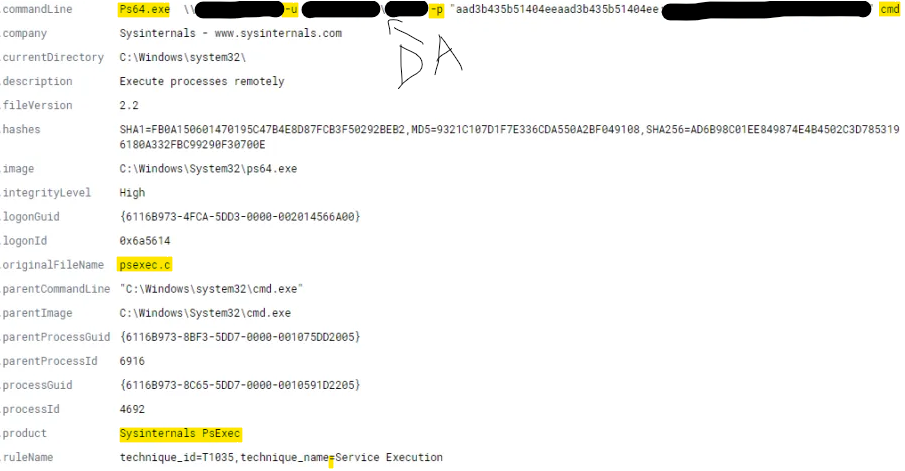
An attacker logged into the RDP Honeypot a few weeks ago and was able to dump credentials and move laterally in 36 minutes. I’ve been seeing more and more ProcDump and less and less mimikatz lately. The attacker attempted to run a couple executables to maintain persistence but these attempts failed. These attempts failed because…
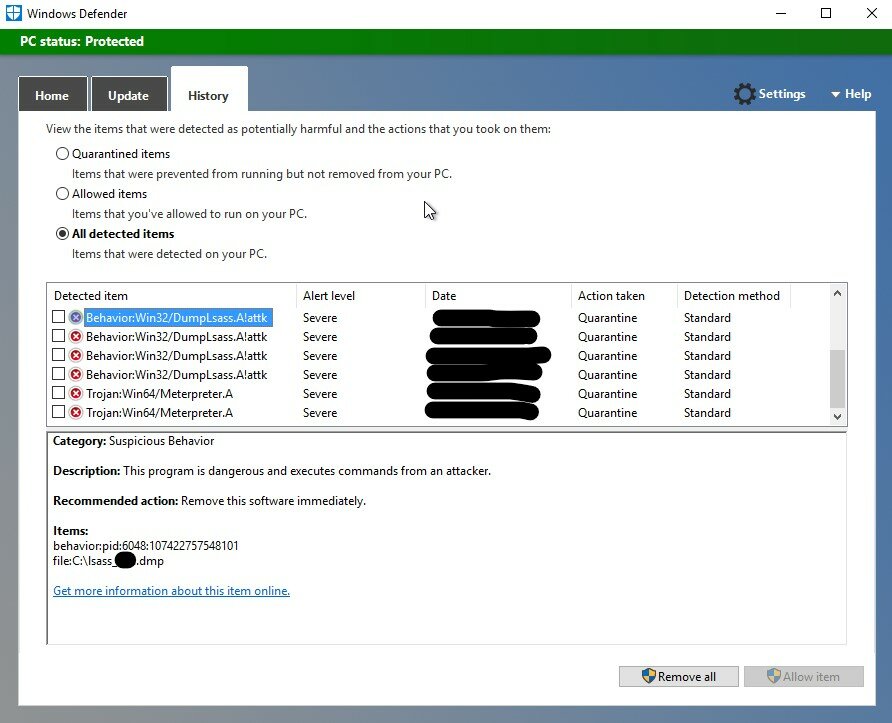
Defender Quarantines Lsass Dumps
An attacker logs into my RDP Honeypot, launches Advanced Port Scanner, attempts to run a Meterpreter reverse shell; and then, dumps Lsass using ProcDump. The attacker, stumbles along the way and does not accomplish their mission. See the timeline, details, summary and IOCs below. Timeline 2:52 – Logon from 185.156.177[.]131 2:55 – Copied Advanced Port…
RDP Honeypotting
I recently stood up a RDP honeypot consisting of a Windows VM with Wazuh and Sysmon. SecurityOnion is setup to monitor traffic to/from the internet for the honeypot. A UTM device is sitting between the honeypot and the internet to block ports, applications and proxy all traffic. I haven’t setup ssl decryption yet but I’m…