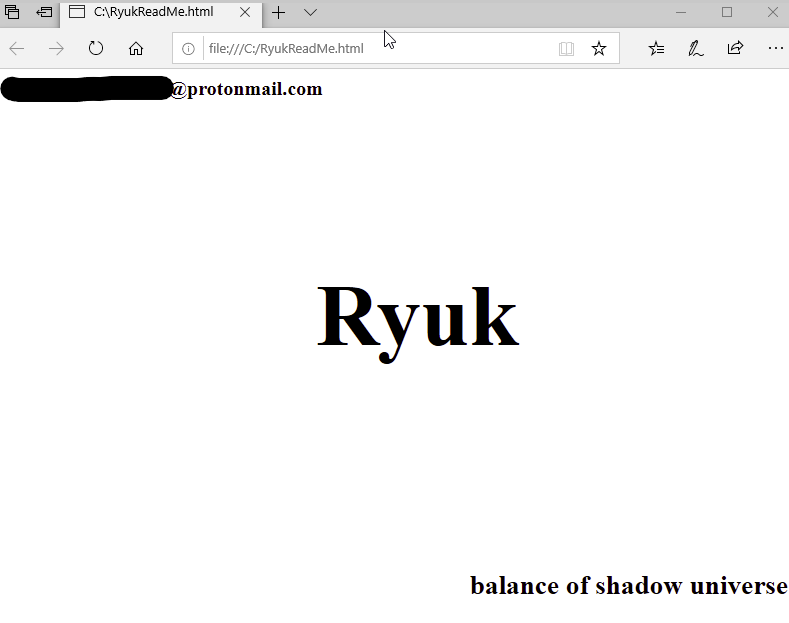
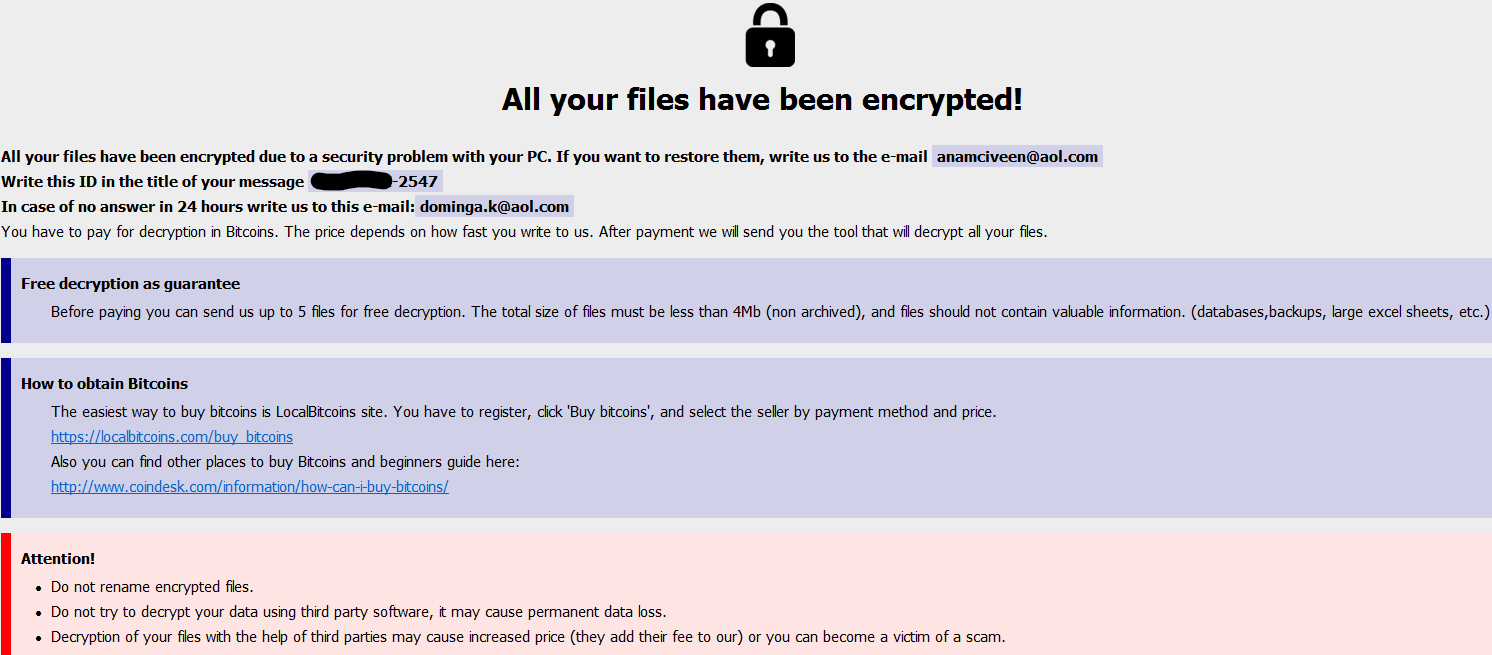
A few days ago, I ran a Trickbot sample in the lab and was quite surprised what occurred. The attackers ran Cobalt Strike across multiple machines within 30 minutes and confirmed hands on activity within 60 minutes. They did additional recon and testing before deploying Ryuk. The attackers were able to go from Trickbot on…
Category: Security
The Dever Ransomware Experience
I was scrolling through social media the other night and came across a friend who posted a screenshot of one of his home lab devices getting ransomwared. I reached out and asked if he wanted help taking a look into what happened and he excitedly said yes! The next 7-8 hours were a blur. I…
Tridium Niagara Vulnerabilities
**If you’ve been contacted by me, it is because your device is on the internet and may be vulnerable to the vulnerabilities identified below. Please read through this and contact me if you have questions. Thanks** What is Tridium Niagara? Tridium is the developer of Niagara Framework. The Niagara Framework is a universal software infrastructure…
Defending Against Emotet
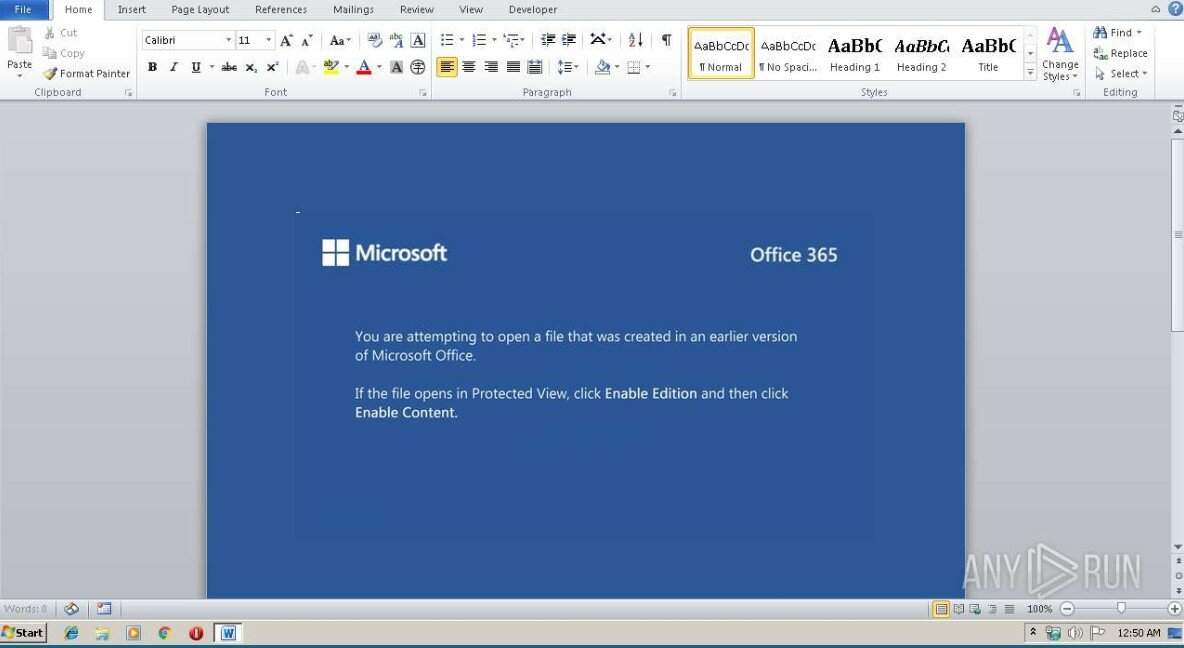
Emotet started making the rounds again a couple months ago. If you work in an enterprise environment you’ve probably seen a sample or two. Here’s an in depth write-up by Brian on Emotet TTPs. Here are a few things you can do to defend against Emotet: Block Macros Block macros from running in Word files…
MouseJack: From Mouse to Shell – Part 2
This is a continuation of Part 1 which can be found here. New/Fixed Mice Since the last blog post, I’ve done some additional testing and it looks like most of the newer wireless mice are not vulnerable to MouseJack. I tested the best-selling wireless mouse on Amazon (VicTsing MM057), Amazon’s choice (AmazonBasics), and one of…
MouseJack: From Mouse to Shell – Part 1

What is MouseJack? MouseJack is a class of vulnerabilities that affects the vast majority of wireless, non-Bluetooth keyboards and mice. These peripherals are ‘connected’ to a host computer using a radio transceiver, commonly a small USB dongle. Since the connection is wireless, and mouse movements and keystrokes are sent over the air, it is possible…
WDigest: Clear-Text Passwords in Memory
What is it? WDigest.dll was introduced in the Windows XP operating system. The Digest Authentication protocol is designed for use with Hypertext Transfer Protocol (HTTP) and Simple Authentication Security Layer (SASL) exchanges, as documented in RFCs 2617 and 2831. Many people think of Digest Authentication as a protocol that is used with Web browsers for…
Kioptrix: Level 1.2 Walkthrough – Vulnhub
Name: Kioptrix: Level 1.2 Date released: 18 April 2011 Author: Kioptrix Download Enumeration Attacker: 10.11.1.7 Target: 10.11.1.10 Initial scan results below Well there aren’t a lot of options so I decided to start with http. I quickly found the login page for phpMyadmin and was able to login with admin as the user and no…
Kioptrix: Level 1 Walkthrough – Vulnhub
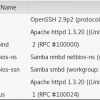
Name: Kioptrix: Level 1 Date released: 17 Feb 2010 Author: Kioptrix Download: https://download.vulnhub.com/kioptrix/Kioptrix_Level_1.rar Initial scan results below Poked around 80/443 and didn’t find anything interesting Discovered OS and Samba version info using Enum4Linux Found an exploit for Samba 2.2.x which can we found here Downloaded and executed the exploit ROOT!! Now let’s look around and…
Offensive Security Certified Professional (OSCP) Review

It’s just another Saturday, I wake up around 6:30 am, get ready and head into the office to start my 12-16 hour day of Penetration Testing with Kali Linux (PWK/OSCP) training from Offensive Security. Although, it’s not like the last 16 Saturdays, today is exam day. OSCP Exam I sat down at my desk around 7:30…